SECURE FILE SHARING WITH TERACRYPTION: WHY IT’S ESSENTIAL FOR MODERN ORGANIZATIONS
- Delta2 Access
- Sep 3, 2025
- 3 min read
Updated: 14 hours ago

Secure File Sharing
In today’s digital environment, secure file sharing is no longer a convenience—it is a business necessity. Sensitive documents such as financial reports, contracts, client data, and board packs are constantly in motion. Without proper controls, these files represent a significant vulnerability. Traditional sharing methods, such as email and consumer-grade platforms, fall short, creating risks of data breaches, regulatory penalties, and reputational damage.
TeraCryption offers a strong, enterprise-level solution designed to safeguard organizations from these risks. Using military-grade encryption, detailed access controls, real-time file sharing, and comprehensive compliance support, TeraCryption guarantees that sensitive files remain secure, accessible only to authorized parties, and fully auditable.
The Challenges of Traditional File Sharing
Organizations frequently depend on email attachments, public cloud storage, or standard file-sharing tools. Although these methods are convenient, they create security risks:
● Accidental Data Leaks: Emails can be misaddressed, forwarded, or intercepted.
● Unauthorized Access: Consumer-grade platforms often lack strict access controls.
● Data Breaches: Weak security makes them prime targets for cybercriminals.
● Compliance Failures: Lack of logs, controls, and audit readiness can violate GDPR, HIPAA, SOC 2, and other frameworks.
● Reputation Damage: Mishandling sensitive data erodes trust among clients, partners, and regulators.
● Version Confusion: Multiple email chains result in outdated or conflicting file versions.
How TeraCryption Solves These Challenges
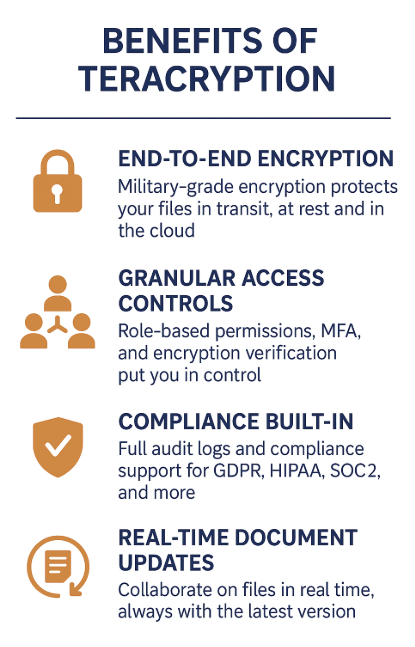
Unbreakable file encryption
TeraCryption secures every file in transit and at rest by encrypting each file with military-grade encryption. Even if files are intercepted, they remain unreadable without proper authorization.
Granular Access Control
● Role-based permissions ensure users only access what they need.
● Selective user sharing controls.
● Group-based restrictions limit file access to trusted users only.
Compliance-Ready Architecture
TeraCryption simplifies adherence to data protection laws and industry regulations:
● GDPR, HIPAA, SOC 2, PCI DSS, ISO, and more.
● Full audit logs record who accessed files, when, and what actions were taken.
● Easy reporting for regulatory audits and compliance reviews.
Real-Time Document Management
● Centralized platform eliminates version confusion.
● Updates are reflected instantly, ensuring stakeholders always work on the latest file.
● Prevents errors and miscommunication in critical workflows.
Complete Visibility and Audit Trails
Logins, file-encryption tracking, and user messaging are recorded. This transparency facilitates compliance, internal governance, and forensic investigations as needed.
Enhanced Reputation and Trust
Organizations that adopt TeraCryption demonstrate a strong commitment to safeguarding sensitive data, enhancing stakeholder trust, and fostering long-term business relationships.
Example Use Cases
● Board Communications: Securely distribute board packs and confidential strategy documents without risk of leaks.
● Legal Practices: Protect attorney-client privilege with encrypted, access-controlled sharing.
● Healthcare Providers: Comply with HIPAA while sharing patient records across networks.
● Financial Services: Safeguard transactions, investment data, and regulatory reports.
Comparative Analysis
Traditional File Sharing | TeraCryption Advantage |
Email attachments, consumer-grade tools. | Secure top layer with random-key encryption. |
Weak or no access controls | Granular, role-based permissions. |
No audit trails | Complete logging and compliance reporting. |
Confusion with multiple versions | Real-time updates, centralized version control |
High compliance risk | Built-in support for GDPR, HIPAA, SOC 2, PCI DSS, and ISO 27002. |
Erodes client trust | Strengthens reputation and governance practices |
Strategic Benefits
These benefits result from applying encrypted file-sharing best practices when storing encrypted files on the local server.
Risk Mitigation: Protects against costly breaches, fines, and legal exposure.
Operational Efficiency: Reduces friction in collaboration by ensuring files remain accurate and secure.
Compliance Assurance: Simplifies audits and demonstrates strong governance.
Reputation Protection: Positions the organization as a trusted partner.
Conclusion
Secure file sharing is not optional—it is a fundamental requirement for any modern organization. Traditional tools cannot keep pace with today’s cybersecurity and compliance demands.
TeraCryption delivers the encryption strength, access controls, compliance tools, and audit capabilities necessary to protect sensitive data, streamline collaboration, and inspire trust. These are examples of a complete file encryption system in practice.
For organizations seeking to strengthen governance, safeguard client data, and stay compliant in an increasingly regulated environment, TeraCryption is the gold standard for secure file sharing.
About TeraCryption
TeraCryption is a leading developer and provider of secure messaging and encrypted file systems for protecting sensitive information at rest and in transit.
Schedule a 30-minute online demo at https://www.teracryption.com/demo with our team of experienced specialists. Feel free to email us at sales@teracryption.com. We're here to help you keep your message communications and files safe and secure!


